I’m gonna be brutally honest with you—when I first started tinkering with IoT devices back in early 2024, security wasn’t my biggest concern. It should’ve been. But like most devs caught up in the buzz of blinking lights and dashboards, I was more hyped about making things “talk” to each other than worrying about who else might be eavesdropping.
Yeah. That changed real quick.
So today, I’m spilling the beans on how I finally got serious about securing IoT devices using MQTT and TLS—two tools I now swear by. This isn’t a technical manual or some copy-paste from a doc site. This is me, in 2025, telling you how it really went down, what I learned, what I screwed up, and how I eventually found my footing in this tangled mess called IoT security.
The IoT Moment I Knew Things Were Bad
Last year, I built this prototype for a smart greenhouse—pretty simple stuff: sensors for humidity, temperature, soil moisture. All communicating over MQTT. The data flowed beautifully into my Node.js backend, and everything looked like a success.
Until a random guy on Reddit posted a screenshot of my exact dashboard—MY dashboard, my project. Same values. Same graphs. And my heart sank.
Turns out I had been transmitting everything over MQTT without encryption. Anyone sniffing the network could read it. Rookie mistake? Maybe. But it was the wake-up call I needed.
MQTT: Love It, But Handle with Care
MQTT, if you’re not familiar, is the de facto protocol for lightweight messaging in IoT. It’s fast. It’s elegant. It uses a publish/subscribe model that’s easy to scale and easy to break if you’re careless.
The beauty of MQTT is that it doesn’t carry the baggage of HTTP. But the catch? It’s not secure out of the box. Like, at all.
You can literally connect to an MQTT broker on port 1883 (the default) and just start exchanging messages with anyone on the same network if there’s no authentication or encryption set up.
That’s why TLS is so freaking important.
Enter TLS: The Grown-Up in the Room
TLS (Transport Layer Security) is what finally brought some peace of mind into my IoT experiments. It encrypts the messages as they travel over the network, turning your “Hey, here’s the temperature” into digital gibberish for anyone without the right keys.
When I first tried setting up TLS with MQTT, I messed it up…badly.
I remember configuring the broker (I was using Mosquitto, BTW) with self-signed certificates I barely understood. Devices refused to connect. Error logs looked like ancient hieroglyphics. I spent two nights staring at them, trying to figure out whether it was the certs, the paths, the permissions, or the phase of the moon causing the issue.
Turns out, it was just a mismatched hostname in the certificate. Dumb mistake. But also one I’ll never forget.
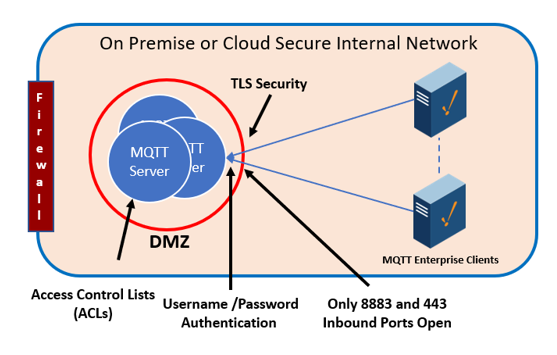
🛠 Real-World Setup: Pain & Progress
Here’s how I now do it, after a LOT of trial and error:
- Every device gets authenticated with a username and password. It’s basic, but it helps prevent random connections.
- TLS is mandatory, not optional. I use Let’s Encrypt if I want proper signed certs. Self-signed if it’s just a lab experiment, but I handle them carefully.
- I disable port 1883 entirely. Only 8883 (the encrypted MQTT port) is open.
- I also limit topic access per device. Like, the moisture sensor shouldn’t be allowed to publish to the fan control topic. Learned that the hard way too.
And the big one?
I always test what happens when something breaks. What happens if a certificate expires? What happens if someone tries to connect without credentials? What does the log say? This used to scare me. Now it excites me, because I know what to expect—and how to respond.
Real-Life Scenario: The Coffee Machine Hack
This one still makes me laugh, but it’s a real warning.
A buddy of mine (let’s call him Ravi) built an IoT coffee machine. The thing brewed based on calendar invites—because, why not? But he left MQTT wide open.
One evening, I connected from my laptop, published a “brew” command repeatedly, and the machine went nuts. Spewing espresso all over his kitchen counter. He thought it was a ghost.
We fixed it. But he learned fast: even harmless devices can be misused without proper safeguards.
Some Small Wins That Made a Big Difference
- I started using client certificates, especially for sensitive devices. It’s a pain to manage, but it’s worth it.
- I added device-level firewalls, like iptables on Raspberry Pis, to limit outgoing connections.
- Logging and monitoring is non-negotiable now. I want to know who connected, from where, and when.
And yeah—my dashboards are locked behind authentication now. That one still stings.
TLS Is Not Enough Alone
Here’s something I didn’t get at first: TLS doesn’t protect against stupid. If your credentials are weak, or you hardcode them into firmware, you’re still vulnerable.
Security is layers. TLS is just one. But it’s a solid, essential one.
My Two Cents (For What It’s Worth)
If you’re building anything with IoT in 2025, treat security like oxygen—you don’t think about it until it’s missing, and then it’s usually too late.
I’m not a cybersecurity expert. Just a developer who got burned, got better, and kept building.
Use TLS. Lock down your topics. Rotate your credentials. Log everything. And maybe, just maybe, your smart fridge won’t turn against you.
Final Words
I’m still learning. Every time I deploy something new, I test it with the mindset of a hacker. It’s not paranoia. It’s preparation.
So if this messy, slightly embarrassing journey helps even one of you avoid the dumb mistakes I made—I’m glad I shared it.
Read our more blogs-How to Pitch Yourself as a Consultant in Emerging Tech Fields