Alright. Gonna be honest — for the longest time, I kinda half-assed APIs security on my small projects. I mean, it’s not like I had a million users hitting my endpoints. Usually just a few teammates or maybe my own frontend app. But man, the minute you leave something even slightly exposed, bots and random scripts sniff it out like blood in the water.
Happened to me last year. Woke up, server logs were ugly. Someone figured out a public endpoint and spammed the life outta it. So yeah… figured it was time to grow up and do proper JWT authentication in my Spring Boot app.
I Knew About JWT… Kinda
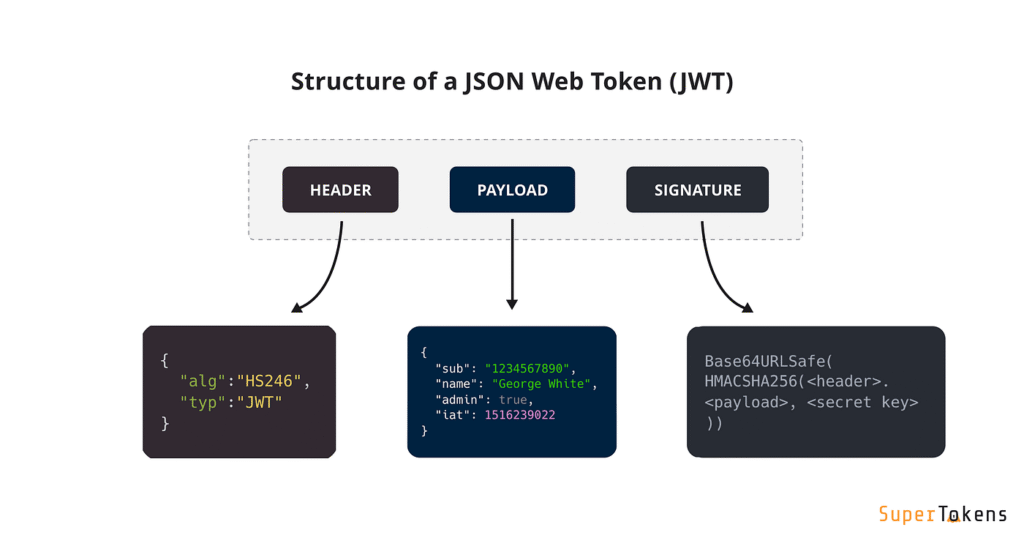
I’d heard people hype up JWTs forever. Knew the basic idea: server gives you a token when you log in, you carry it around in your requests, and the server uses it to check you out. No need for sessions. No saving stuff in memory. Fine, cool, whatever.
But actually wiring it up in Spring Boot? Eh, took me a minute.
Not Gonna Lie, Spring Security Is Kinda Weird Sometimes
Here’s the thing — Spring Security is both powerful and unnecessarily confusing. There’s like five ways to do everything, and you’ll always land on some Stack Overflow answer from 2018 that only half works now.
In the end, the trick was getting a custom filter running before the security context did its thing. So I basically made a JWT filter that checked the Authorization header on every request. If it saw a token, it verified it, pulled out the claims, and set the user context. If not, request carried on without a logged-in user.
Simple in theory. Broke my app like three times before it worked.
Couple Dumb Things I Forgot
- Forgot to disable CSRF protection for the API. Kept getting blocked on POST requests. Took me way too long to remember that stateless APIs don’t need CSRF tokens.
- Messed up the secret key config at first. Pro tip: don’t hardcode it in your config file if you plan on sleeping at night.
- Left a token expiration set for, like, 100 years as a test. Forgot to change it. Not ideal.
Once It Worked Though… Clean
Honestly, once the thing finally behaved, it felt good. No sessions. No weird state hanging around. Every request just carried its token, and either you were legit or you weren’t.
Also loved being able to toss stuff like roles and permissions right inside the JWT claims. Meant I didn’t need to hit the database every time a user tried to do something restricted. Token had everything I needed.
The Annoying Stuff
Not gonna pretend it was all sunshine. Debugging JWT errors kinda sucks. If your secret’s off, or you accidentally encode something wrong, you just get these 403 responses with no helpful logs. You end up sprinkling debug prints all over your filters like confetti.
And writing integration tests for endpoints behind JWT protection? Mildly annoying. Had to manually generate valid tokens for test cases. Not hard, just tedious.
Should You Bother?
Honestly? Yes. If your API talks to anything besides your local machine, lock it down. JWT is one of those things that seems annoying upfront, but once you nail it, it saves you headaches down the road.
I’m not saying it’s perfect. There’s stuff you gotta watch for — like making sure the tokens expire, not cramming sensitive data in there, and thinking about refresh tokens if your sessions are long-lived. But for your average API? It’s solid.
Final Thought Before I Crash
If you’re working in Spring Boot and still relying on old-school sessions or, worse, just assuming “it’s a small app, nobody will mess with it” — yeah, don’t. People are weird. Bots are weirder.
Grab a JWT library, wire up a filter, test it out. Break it a few times. You’ll figure it out. It’s one of those things that’s more annoying in your head than it is once you actually build it.
Read more posts:- How I Learned to Wire My IoT Data to a Web Dashboard with Node-RED & MQTT